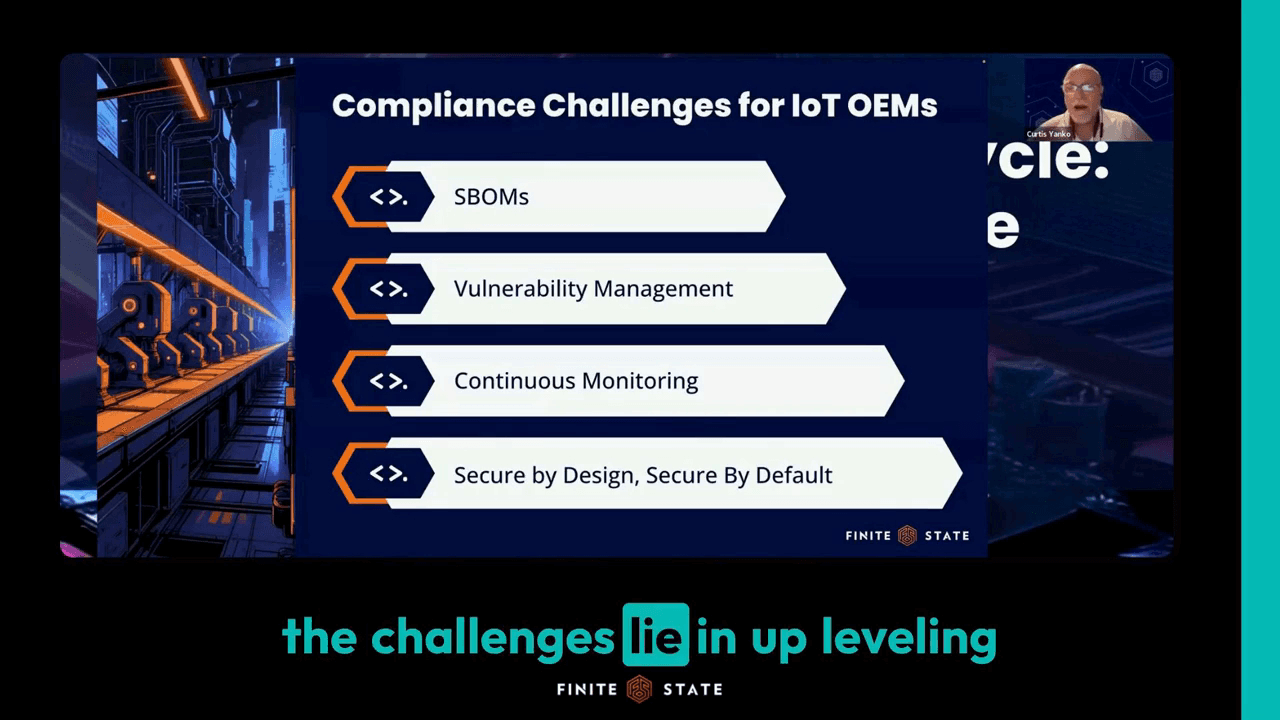
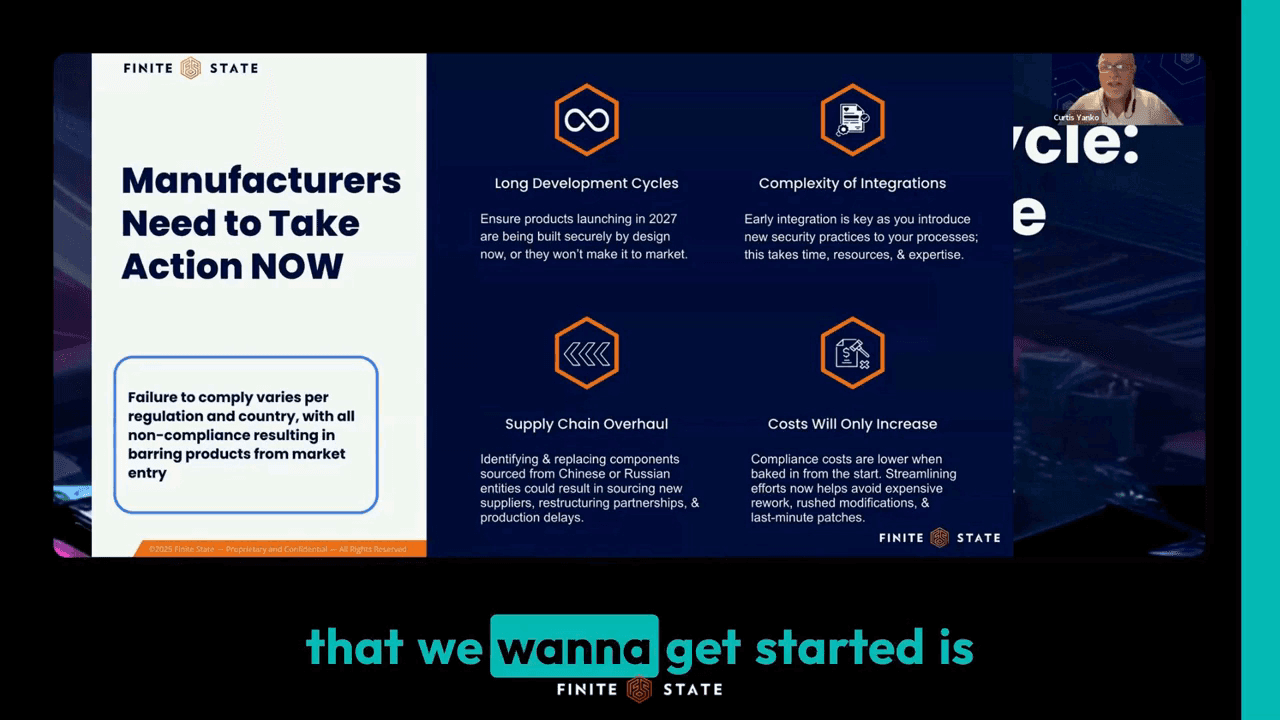
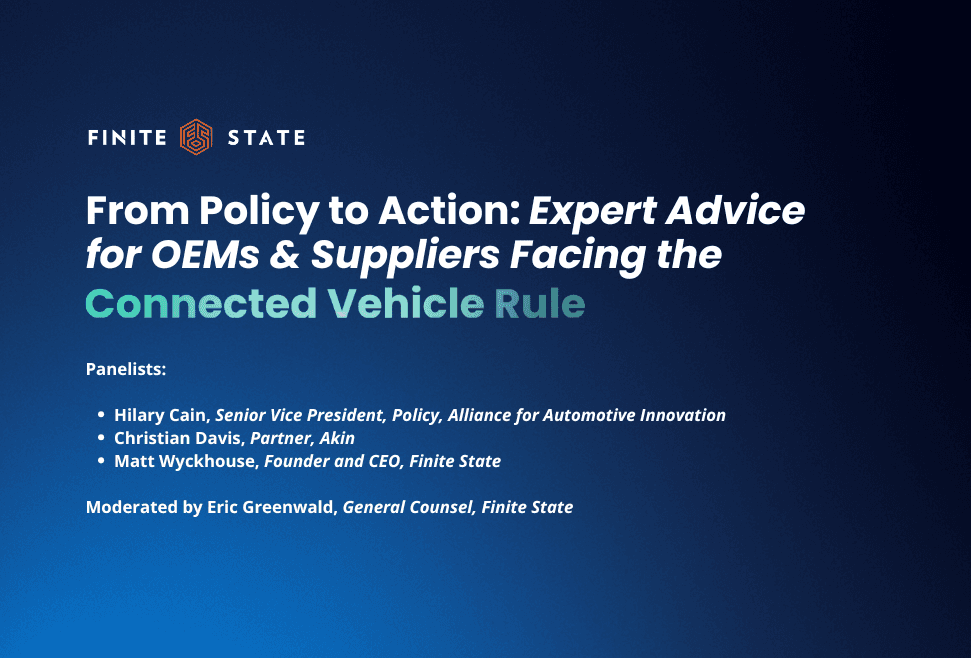
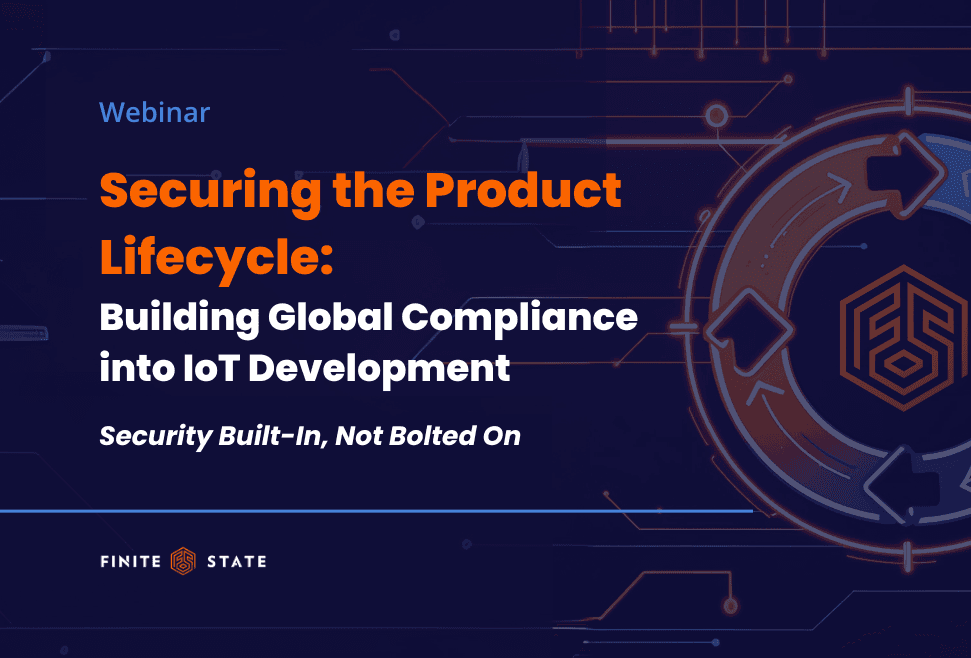
Security Expertise On-Demand
Product Security Theater
Experience the future of product security through our immersive video content. From Al-powered analysis to real-world case studies, discover how industry leaders protect their digital assets.
34 results