
Connected Devices
IoT & Embedded Security
Secure every release. Prove compliance continuously. Automate the work in between.
Finite State is the Product Security Automation Platform for connected devices, uniting firmware and source intelligence with automated workflows that prioritize real exposure and produce audit-ready security and compliance outcomes.
The system of record for shipped reality, featuring an SBOM Exchange, Vulnerability Hub, and Reachability Engine. It reduces vulnerability noise by up to 90% through analyzing reachability and execution context to prove which threats are executable.
Noise Reduction
using reachability-driven prioritization
Integrations
DevSecOps tools and CI/CD integrations
Vulnerability Sources
and exploit intelligence sources
Automate product security across every release.
The Finite State Platform connects design artifacts, binary reality, and vulnerability monitoring into a single system of record that evolves with your product.
Fragmented Security Work Leads to Audit Gaps
Misses firmware and third-party binaries.
Lack developer context and policy gates.
Creates noise, duplication, and inconsistent audit outcomes.
Misses firmware and third-party binaries.
Lack developer context and policy gates.
Creates noise, duplication, and inconsistent audit outcomes.
Correlate documentation, source code, and deep binary analysis to create a trusted picture of what you ship. That means fewer gaps, fewer assumptions, and portfolio-wide visibility you can stand behind.
Reachability, exploit context, policy, and VEX workflows work together to prioritize real exposure.
A maintainable threat model connects threats to risks, mitigations, requirements, and verification.
Clause- and control-to-evidence traceability produces audit-ready evidence packs and reporting.
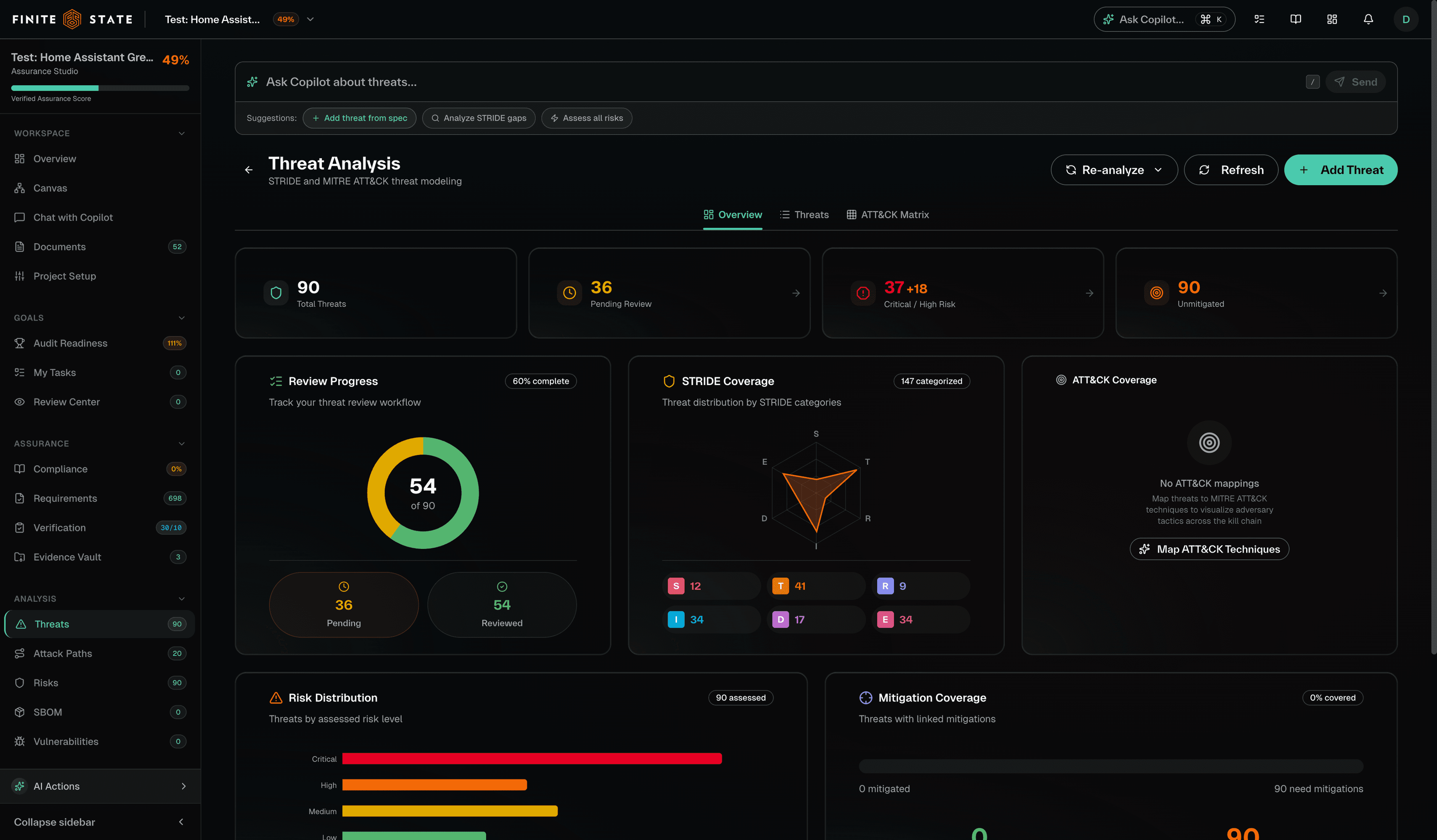
Consolidate analysis, SBOM management, VEX workflows, and evidence generation to accelerate security work and produce trusted compliance outputs.

Reduce friction across the OEM ecosystem with consistent, audit-ready security artifacts—SBOMs, VEX, verification evidence, and reports—aligned to shipped software.
See how Finite State helps organizations strengthen product security and meet compliance requirements.
Secure every release. Prove compliance continuously. Automate the work in between.