Manage risk across your software supply chain
Finite State's Next Gen platform features extended SBOM management that ingests and aggregates data from over 150 external sources, giving security teams a unified and prioritized risk view with unprecedented visibility across the software supply chain.
Our Next Gen Platform:
- Generates, collects, visualizes, and distributes SBOMs in your supply chain
- Ingests scans from 150+ scanners and feeds, unifying all the tools that defend your product or system in the full context of your environment
- Provides remediation guidance that aggregates and reconciles results across all scans, generated or ingested, for context-aware recommendations
- Decomposes a product or asset into its many components through world-class binary SCA and enhanced SBOM capabilities so you get a laser-focused risk assessment
- Conveys a product's or system's risk levels through its robust scoring methodology, backed by sophisticated risk prioritization
- Imports and exports all VEX formats, with advanced vulnerability intelligence correlation
-1.png?width=4114&height=2992&name=Update%20Overview%20Designs%20for%20S4%20Scope%20-%20ASOC-286%20(1)-1.png)
Visibility & Protection
Our ability to ingest scans from 150+ scanners and feeds unifies your arsenal of tools so you can ascertain the security of your product or system in full context.
Simplicity & Scalability
Free your processes from costly, slow, and cumbersome manual testing. Whether you have one device or hundreds, simply upload the firmware of all your devices and our automated platform will do the rest, often in less than one business day.
Intuitive Scoring System
Our streamlined scoring methodology effectively conveys the risk level of your product or asset through a straightforward numerical scale, backed by sophisticated risk prioritization.
Key Features
Software Composition Analysis delivers:
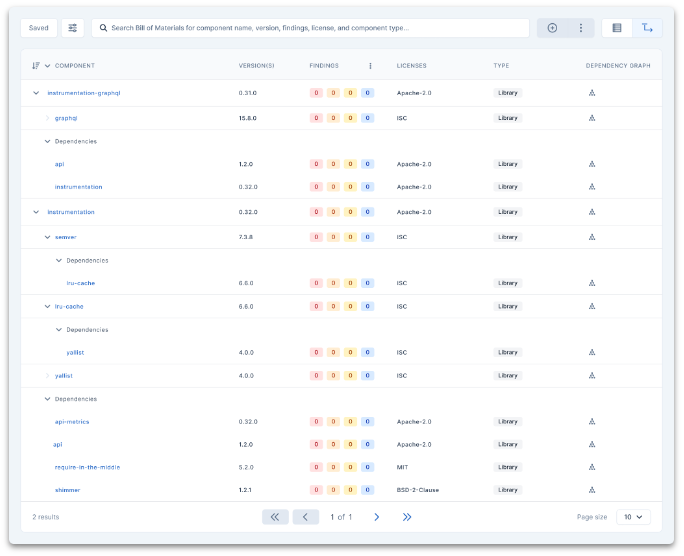
- SBOMs: (Software Bill of Materials) Full visibility into all software components such as binaries, libraries, open source software (OSS), third-party components, embedded software, drivers, etc.
- Visibility into Third Party & Open Source Risk: Security risks inherited by your vendors and suppliers, including legal & compliance risk from unknown, undisclosed, or expired licenses
- Robust VEX Support: Insecure configurations, hard coded credentials, cryptographic materials, and other possible sources of weakness
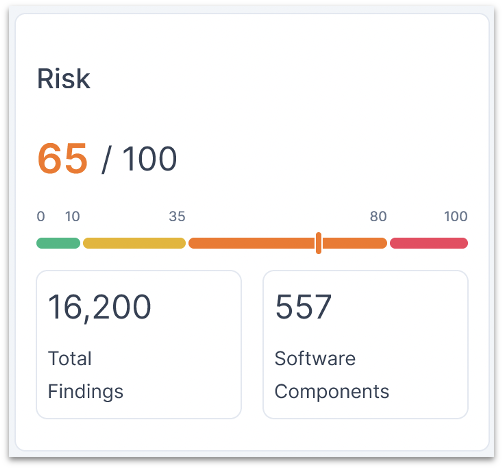
Comprehensive Risk Profile
A unified view of your product and supply chain risks with a risk score that indicates level of urgency. You get a streamlined scoring methodology that effectively conveys risk levels of a product or asset through a straightforward numerical scale, backed by sophisticated risk prioritization.
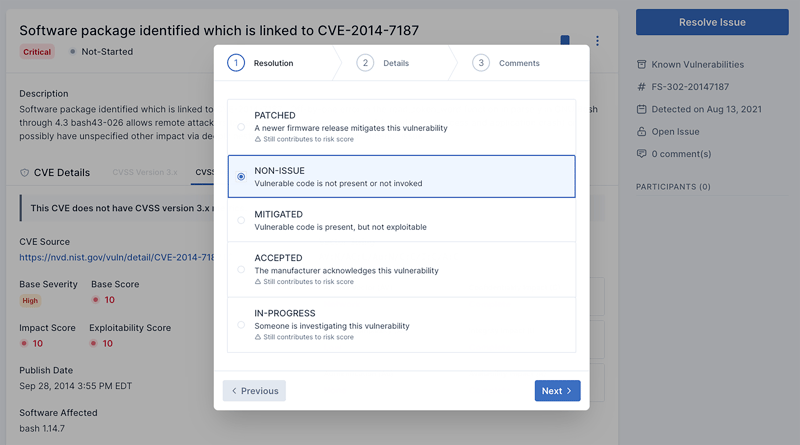
Issue Management
Advanced remediation guidance that de-dupes and reconciles results across all scans, generated or ingested, for context-aware recommendations. A way to quickly prioritize and manage security issues. Reduce friction between development teams and product security teams by providing remediation guidance with the largest risk reduction ROI.
Compliance Guidance
Meet regulatory requirements with essential information necessary so teams can address compliance gaps across the automotive, energy and medical device industries.
Advanced Reporting & Analytics
Enhanced SBOM capabilities to decompose a product or asset into its many components for a laser-focused risk assessment, or a Summary Report for business leaders. Guided by our intuitive scoring system, share insights and analytics with internal and external stakeholders via our easy and robust reporting function.
Finite State is SOC 2 Type 2 Certified!
Helpful Resources
Finite State Platform Solution Brief
Learn more about the Finite State Platform and how it works.

Preparing your organization for EO 14028
President Biden's Executive Order on Improving the Nation's Cybersecurity will affect more than just those organization selling into the Federal government. Learn how to prevent your organization from falling behind.

Finite State vs AppSec
Learn how Finite State differs from and works with traditional Application Security tools to fill the critical gaps in your product security.

SBOM Minimum Requirements
Learn what NTIA considered the minimum standards for a Software Bill of Materials (SBOM) and why it's so important to have one.