Last week, the cybersecurity firm FireEye discovered a watershed supply chain attack that targeted their firm as well as multiple government agencies. This attack targeted the SolarWinds Orion product, which is a Windows-based network management platform used by thousands of IT organizations globally. Software updates for Orion were trojanized at some point in the development and deployment process, resulting in a backdoor (known as SUNBURST) being installed on SolarWinds Orion customers’ networks. The backdoor, inserted into the Orion software by attackers prior to being published to the update server, is custom, beaconing malware that uses a combination of blending in with SolarWinds data/traffic and steganography to avoid detection. Given the information that was accessed as well as the level of sophistication involved, FireEye believes this to have been a state-sponsored attack.
This is not the first time that attackers have exploited software supply chains to gain access to critical information or infrastructure, and we don’t believe that it will be the last. We are heartened by the support that FireEye, SolarWinds, and other victims have received from the cybersecurity community and want to emphasize how critical it is that we act quickly and come together to prevent these types of attacks in the future.
Why supply chain attacks are so effective and devastating
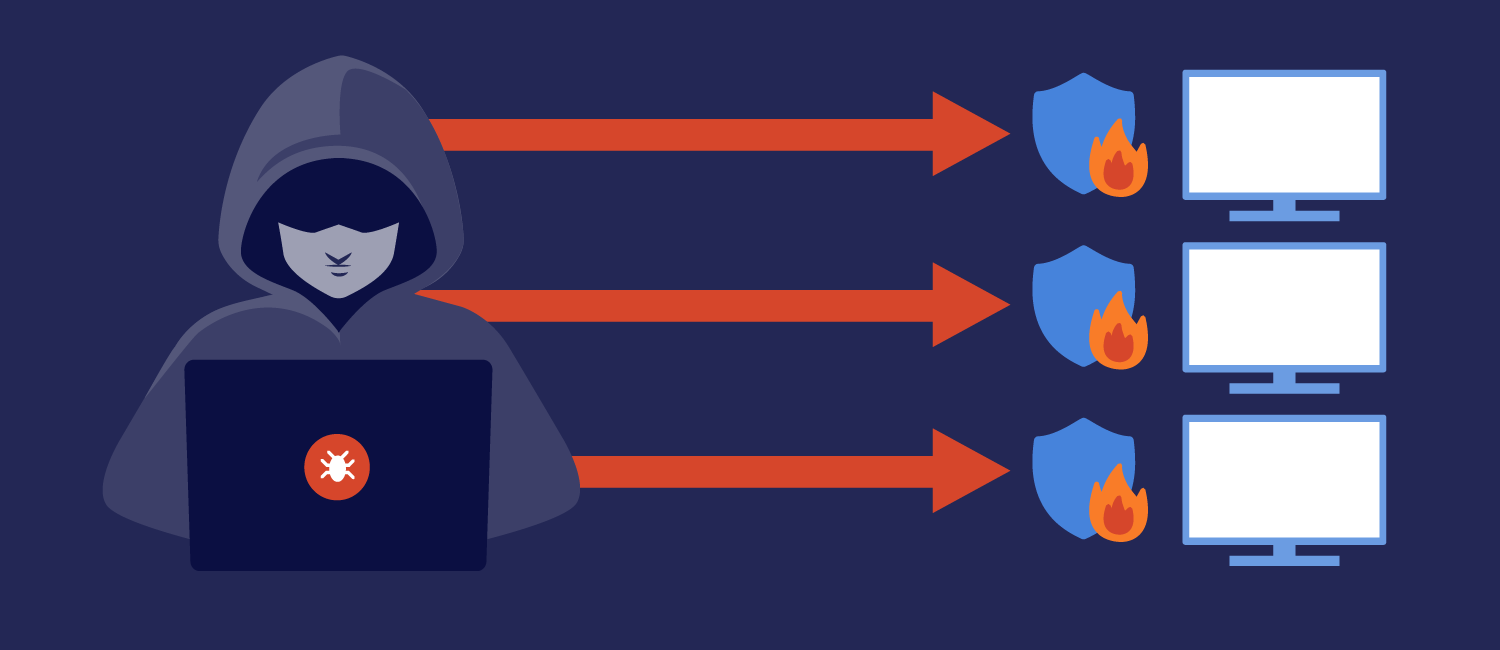
If you are a malicious actor who is attempting to gain access to critical information from a number of sources, you could very well try to attack each business or organization individually. If those entities have robust security measures in place (for example, if they are a government agency or a cybersecurity firm like FireEye), then you’re probably going to have a difficult time.
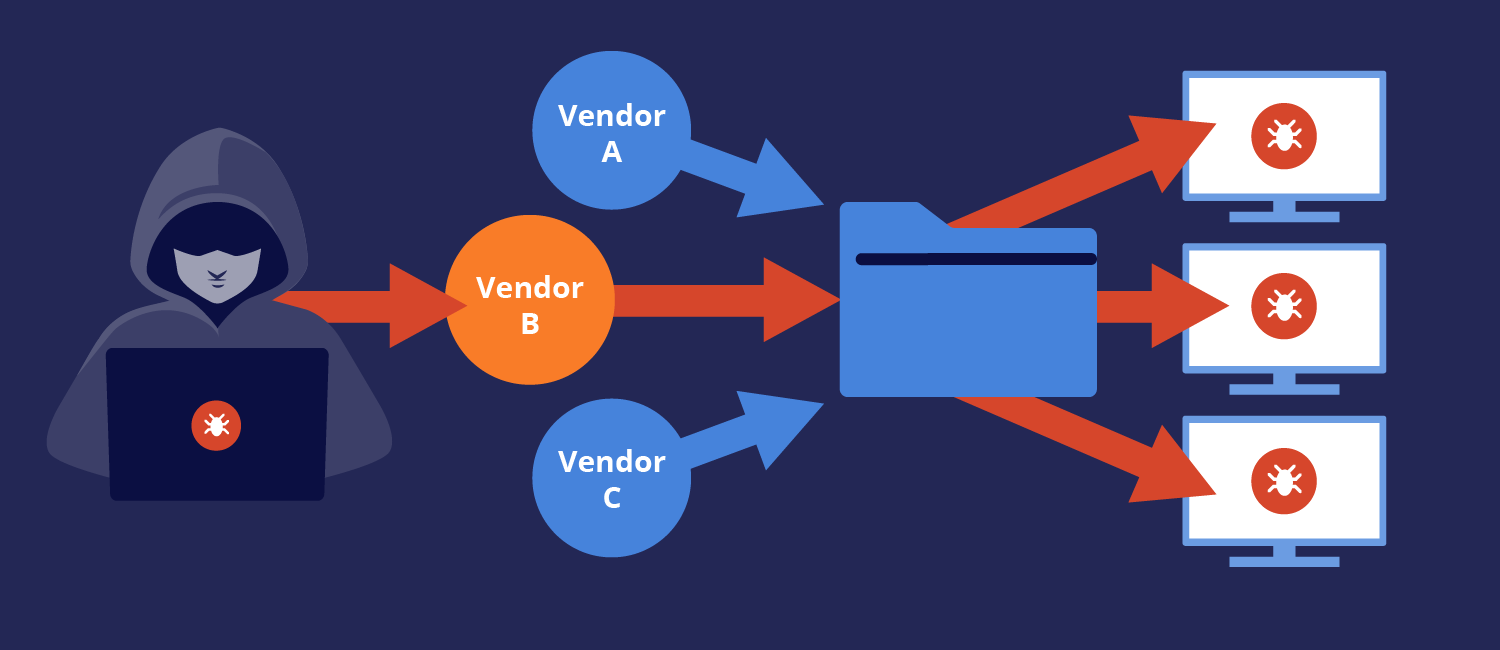
If, instead, you can manage to create a backdoor (or find an existing one) somewhere along the supply chain of a piece of software that is widely used, your chances of being able to breach the security of the aforementioned organizations has not only increased significantly, but you need only exploit a single weak link in order to gain access to multiple networks. One carefully crafted backdoor in a vendor’s supply chain can give an attacker access to all of that vendor’s customers.
This is the reality that we are facing as an industry. It’s important to recognize that advanced adversaries are targeting software and firmware supply chains, and that without solutions that can detect and verify software components we are likely to see more attacks at this devastating scale—or worse. Attackers have repeatedly shown that they have the capability to access our critical infrastructure, including our power grids. Countless medical devices, building systems, and industrial control systems rely on software with complex and opaque supply chains that utilize third-party, proprietary, and open source components.
These opaque supply chains make it hard for software developers and device manufacturers to detect vulnerabilities, and even harder for end users to do so. As a result, if you are targeted by an advanced attacker, it is extremely difficult to defend yourself.
What do we need to do to prevent supply chain attacks?
This attack is a turning point for the security community. It highlights a robust need for better verification throughout the supply chain. Understanding all of the components and detailed functionality in modern software may be a challenging problem to solve, but it is solvable.
The first step is to increase transparency in the supply chain. One of these approaches is for everyone to produce a Software Bill of Materials (SBOM) for software packages, updates, and connected device firmware. This would allow developers and manufacturers to gain a deeper understanding of their software components, which is a critical first step in understanding the risks and vulnerabilities introduced by software supply chains. There are also a number of automated tools emerging on the market that would allow security teams to verify software components at a much deeper level. These tools, such as the Finite State Platform, can be utilized throughout the product security lifecycle—during development, before release, and with each software update that is issued.
Software developers and device manufacturers need to ensure that they’re adopting a robust product and application security approach and deeply integrating security into their development processes. That means that manual and automated testing should be used to ensure the quality and security of the software at each stage of development—from unit testing and code reviews through final testing. Automated security testing tools that leverage Static Application Security Testing (SAST), Software Composition Analysis (SCA), and Dynamic Application Security Testing (DAST) can form the foundation for a rigorous and scalable security testing process. Finally, it is important that developers and manufacturers use standardized build systems and verify the final builds with SAST and DAST techniques. Keep in mind that supply chain attacks can target the build system, so this final step is critical.
Asset owners—especially those who are operating critical networks that are likely to be the target of sophisticated adversaries—should be working directly with vendors to understand what’s inside their software via requesting SBOMs. Additionally, asset owners should be verifying the authenticity of their software and firmware updates via signature or hash checks to avoid watering hole attacks. In some instances, it may even make sense for the asset owner to unpack and scan the software or firmware updates themselves, which is an approach that we support for some of our customers.
At the end of the day, mitigating software supply chain security risks will only be possible if we have software developers, device manufacturers, asset owners, and regulators working together to create more transparent supply chains. In a world that is now more connected than ever, only collaboration at every level will ensure that we remain secure.
Subscribe to Our Blog
Get the latest posts delivered straight to your inbox weekly.
Share this
You May Also Like
These Related Stories

SolarWinds SUNBURST: An Intrusion, Attack, or Act of War?
Provenance: What it Can and Can’t Tell Us About Connected Device Risk


