DETECT | REMEDIATE | COMPLY
Take Control of Connected Device Risk
Uncover vulnerabilities in source code, binaries, and third-party components, and consolidate risks into one unified view for more effective threat management across your product portfolio.

.png?width=177&height=80&name=Hubbell.svg%20(1).png)

Engineered for Product Security Teams
Finite State is built to help you tackle the unique challenges of connected device security with confidence, whether you're facing long lifecycles, complex supply chains, or a lack of vendor transparency.
- Detect vulnerabilities in source code, binaries, open-source software, and third-party components throughout the SDLC
- Manage & monitor multiple software bill of materials (SBOMs) and vulnerabilities throughout your product's lifecycle
- Prioritize & mitigate in real-time, with remediation guidance and 150+ DevSecOps integrations
- Comply with regulations like the EU CRA, FDA's Section 524B, and more

Discover what's putting your connected devices at risk — and how to fix it.

Find what other tools miss
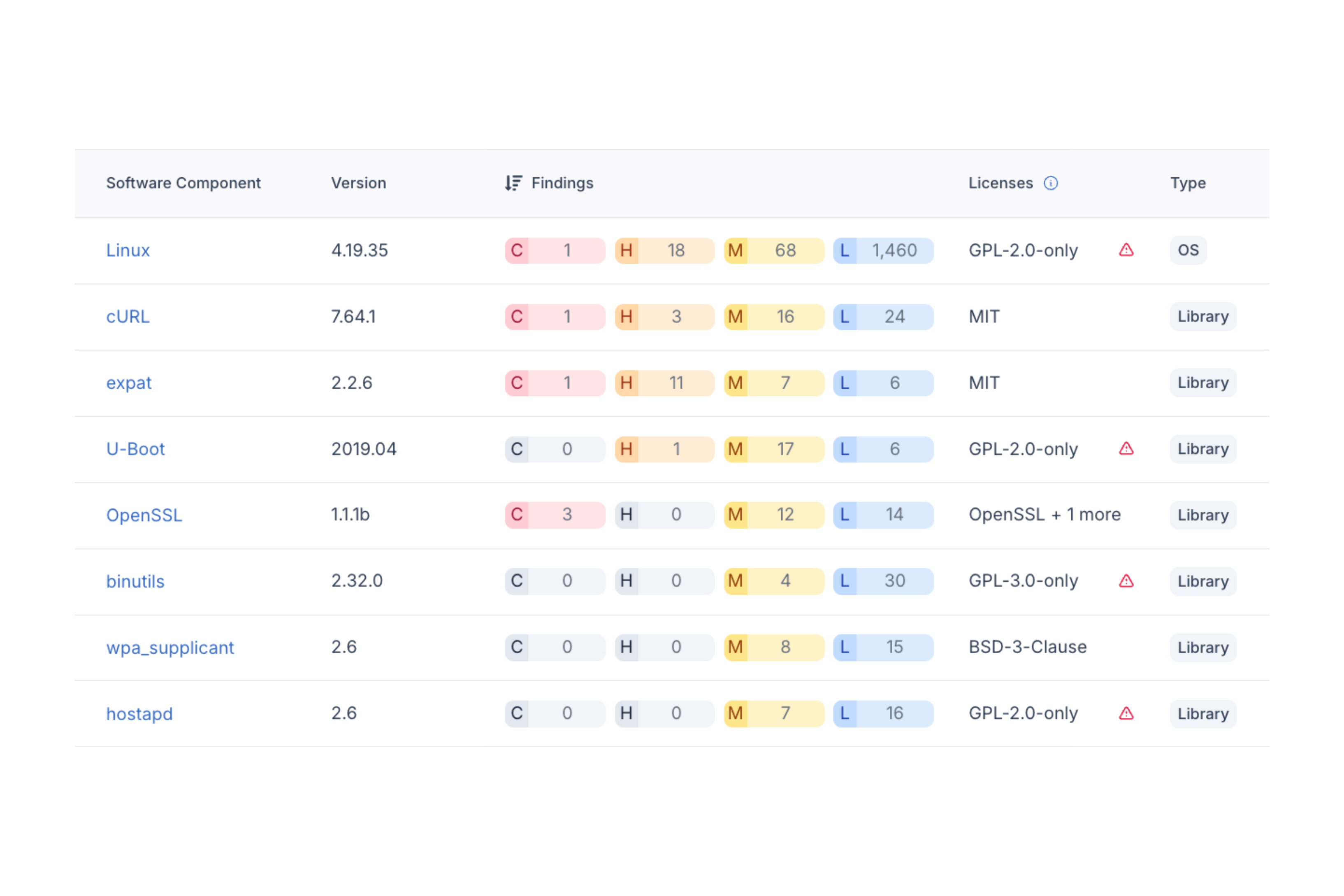
Scan any binary or source code—regardless of origin or format—and reveal the makeup of even your most opaque firmware or tightly integrated software. Uncover the hidden risks you can't afford to miss in legacy systems and third-party components and get unmatched visibility into any device.
- Industry-leading analysis
- Vulnerability enrichment from 200+ threat sources
- Protection for legacy products and cutting-edge IoT
.png?width=719&height=479&name=2%2c162%20(4).png)
Remediate what matters most
Eliminate noise and quickly prioritize and address risk across your portfolio to ship secure products that protect your organization from reputational damage, financial penalties, and loss of access to markets.
- Use risk scoring to prioritize actions based on exploit and severity
- Automate fixes and unlock developer-friendly remediation recommendations
- Access 150+ security integrations for seamless workflows

Fortify your entire product line
Efficiently manage vulnerabilities throughout your device's lifespan and protect everything from a simple sensor to your most complex systems across your entire DevSecOps lifecycle.
- Ensure continuous protection without disrupting workflows
- Access real-time remediation for devices often overlooked by other platforms
- Reduce risk and strengthen customer trust in connected device security

.png?width=3750&height=2500&name=Integration%20(1).png)
Broad Compatibility & Integrations
150+ security integrations and support for:
- 18+ programming languages
- 130+ container, archive, and binary formats
- 30+ binary instruction set architectures
- 40+ package managers
- 200+ threat intelligence and vulnerability sources
Achieve Compliance Beyond SBOMs
Build securely by design and manage and monitor vulnerabilities throughout the lifecycle of your product to comply with ever-evolving global regulations.
- Get audit-ready with end-to-end SBOM management
- Find, prioritize, and fix issues without disrupting development
- Monitor your entire product lifecycle
- Automate reporting in SPDX & CycloneDX

Level up your product security program
Evaluate the current state of your product security readiness and examine your supply chain remediation.
What truly distinguishes them is their personalized customer support. The Finite State team is consistently available to address inquiries, provide expert guidance toward optimal solutions, and demonstrate a genuine willingness to consider customer feedback for feature enhancements.
The best part of working with Finite State is continuous monitoring of security risks. Views help to identify the risk and security vulnerabilities.
Finite State provides a holistic approach to analyzing devices, and the supply chain that underpins them.... We are excited to form this partnership to further support our customers with shifting security left into the design and development of these innovative products.
