Overviewing the Realities of Runtime Application Security
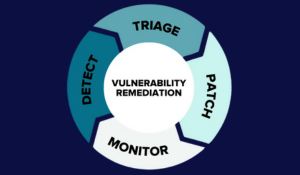

Overviewing the Realities of Runtime Application Security
Oct 2, 2024 4:22:12 PM
12
min read
Software Supply Chain Risk & Mitigation: Webinar with Cassie Crossley


Software Supply Chain Risk & Mitigation: Webinar with Cassie Crossley
Oct 2, 2024 4:15:41 PM
1
min read
Navigating Compliance Requirements with SBOMs
%20(4).png?width=761&height=403&name=Blog%20header%20(300%20x%20175%20px)%20(4).png)
%20(4).png?width=761&height=403&name=Blog%20header%20(300%20x%20175%20px)%20(4).png)
Navigating Compliance Requirements with SBOMs
Sep 4, 2024 5:22:39 PM
3
min read
The In-Depth Guide to Shift-Left Testing


The In-Depth Guide to Shift-Left Testing
Sep 4, 2024 5:10:52 PM
5
min read
All You Need to Know About Open Source License Compliance


All You Need to Know About Open Source License Compliance
Sep 4, 2024 4:53:00 PM
6
min read
10 Major Java Vulnerability Types that Threaten Your Software
-1.png?width=761&height=403&name=Blog%20header%20(300%20x%20175%20px)-1.png)
-1.png?width=761&height=403&name=Blog%20header%20(300%20x%20175%20px)-1.png)
10 Major Java Vulnerability Types that Threaten Your Software
Sep 4, 2024 4:26:35 PM
8
min read
Shift Left Security: Protect Your Dev Life Cycle with Software Composition Analysis

Shift Left Security: Protect Your Dev Life Cycle with Software Composition Analysis
Aug 16, 2024 5:17:29 PM
7
min read
A Critical Look at Cyber Security Investment


A Critical Look at Cyber Security Investment
Aug 13, 2024 6:30:43 PM
3
min read
NIS2 Directive Compliance: Practical Tips for Product Security Teams
NIS2 Directive Compliance: Practical Tips for Product Security Teams
Aug 1, 2024 9:00:00 AM
4
min read
The Comprehensive Guide to FDA Medical Device Regulations


The Comprehensive Guide to FDA Medical Device Regulations
Jul 26, 2024 12:36:06 PM
6
min read
Navigating the EU Cyber Resilience Act: Essential Insights for Product Security Teams


Navigating the EU Cyber Resilience Act: Essential Insights for Product Security Teams
Jul 19, 2024 9:00:00 AM
4
min read
New Enhanced Dependency Capabilities!
.png?width=761&height=403&name=Tran%20Dep%20July%202024%20(2).png)
.png?width=761&height=403&name=Tran%20Dep%20July%202024%20(2).png)
New Enhanced Dependency Capabilities!
Jul 16, 2024 11:15:00 AM
4
min read
Six Things to Consider When Evaluating Software Security Solutions

Six Things to Consider When Evaluating Software Security Solutions
Jul 3, 2024 10:18:29 AM
2
min read
MergeBase’s Bob Lyle Presents at GSMA FASG #29, Istanbul


MergeBase’s Bob Lyle Presents at GSMA FASG #29, Istanbul
Jul 2, 2024 11:32:49 AM
2
min read
CISA's Secure Software Development Attestation Form: How SBOMs and Connected Device Security Can Help


CISA's Secure Software Development Attestation Form: How SBOMs and Connected Device Security Can Help
Jun 18, 2024 4:06:32 PM
4
min read
