Critical Java Log4j Vulnerability
%20(1)-2.png?width=761&height=403&name=Blog%20header%20(300%20x%20175%20px)%20(1)-2.png)
%20(1)-2.png?width=761&height=403&name=Blog%20header%20(300%20x%20175%20px)%20(1)-2.png)
Critical Java Log4j Vulnerability
Aug 1, 2022 8:00:00 AM
2
min read
Should I worry about my pacemaker being hacked? with Errol Weiss & Phil Englert


Should I worry about my pacemaker being hacked? with Errol Weiss & Phil Englert
Jul 22, 2022 2:16:45 PM
2
min read
Electric Vehicle Cybersecurity: What Are the Risks?


Electric Vehicle Cybersecurity: What Are the Risks?
Jul 15, 2022 9:15:00 AM
4
min read
How in the World Do You Measure Cybersecurity, Anyway? with Michael Daniel


How in the World Do You Measure Cybersecurity, Anyway? with Michael Daniel
Jul 7, 2022 10:30:00 AM
14
min read
Incident Response: Instill Confidence in Your Connected Products


Incident Response: Instill Confidence in Your Connected Products
Jun 28, 2022 2:15:00 PM
3
min read
Securing the DevOps Pipeline - You Can Do It the Way Intel Does! - with Darren Pulsipher


Securing the DevOps Pipeline - You Can Do It the Way Intel Does! - with Darren Pulsipher
Jun 23, 2022 10:00:00 AM
12
min read
How Hard Is It to Launch an Offensive Cyber Operation? With TJ White


How Hard Is It to Launch an Offensive Cyber Operation? With TJ White
Jun 14, 2022 9:00:00 AM
16
min read
3 Key Things to Know about Binary Software Composition Analysis (SCA)


3 Key Things to Know about Binary Software Composition Analysis (SCA)
Jun 8, 2022 10:30:56 AM
4
min read
Preventing Git Rebase Fights
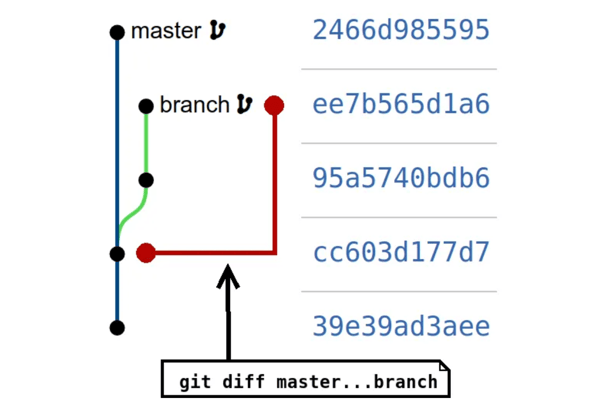

Preventing Git Rebase Fights
Jun 6, 2022 5:47:00 PM
6
min read
Git V: An Optimal Git Branching Model
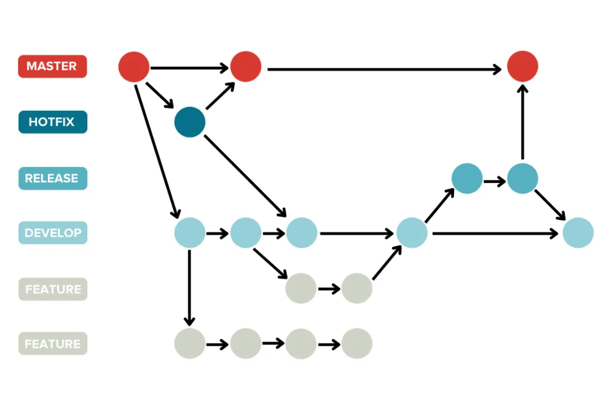

Git V: An Optimal Git Branching Model
Jun 3, 2022 2:52:00 PM
11
min read
The SBOM Is Coming, with Allan Friedman


The SBOM Is Coming, with Allan Friedman
Jun 2, 2022 12:12:35 PM
15
min read
Product Security Teams: How the Heck Do You Run Them? with Josh Corman

Product Security Teams: How the Heck Do You Run Them? with Josh Corman
May 19, 2022 2:35:53 PM
18
min read
Top 6 Ways Product Security Affects Your Bottom Line


Top 6 Ways Product Security Affects Your Bottom Line
Mar 30, 2022 10:36:25 AM
4
min read
When Dependabot Is Worse Than Nothing: Log4J As A Sub-Dependency


When Dependabot Is Worse Than Nothing: Log4J As A Sub-Dependency
Mar 16, 2022 4:30:00 PM
5
min read
What Is Product Security?


What Is Product Security?
Mar 9, 2022 2:10:31 PM
3
min read

.png?width=812&height=509&name=fs-background-texture-02-1%20(blog).png)