How Artificial Intelligence is Revolutionizing Supply Chain Security in 2025


How Artificial Intelligence is Revolutionizing Supply Chain Security in 2025
Mar 7, 2025 1:27:57 PM
3
min read
The Business Case for IoT Security: Beecham Research Highlights the Growing Risks & Opportunities


The Business Case for IoT Security: Beecham Research Highlights the Growing Risks & Opportunities
Feb 28, 2025 1:57:12 PM
1
min read
Top 5 Software Supply Chain Security Threats in 2025
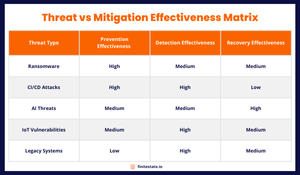

Top 5 Software Supply Chain Security Threats in 2025
Feb 25, 2025 12:36:56 PM
6
min read
How Effective Is Your Software Supply Chain Security? A Framework for Assessment


How Effective Is Your Software Supply Chain Security? A Framework for Assessment
Feb 13, 2025 2:27:32 PM
5
min read
CRA Compliance Made Simple: Addressing Common Software Supply Chain Security Obstacles


CRA Compliance Made Simple: Addressing Common Software Supply Chain Security Obstacles
Dec 6, 2024 3:52:36 PM
3
min read
Software Supply Chain Security Under the EU Cyber Resilience Act


Software Supply Chain Security Under the EU Cyber Resilience Act
Dec 6, 2024 1:36:44 PM
3
min read
Seven Practical Ways to Improve Your Software Supply Chain Maturity


Seven Practical Ways to Improve Your Software Supply Chain Maturity
Oct 4, 2024 3:13:14 PM
6
min read
All You Need to Know About Open Source License Compliance


All You Need to Know About Open Source License Compliance
Sep 4, 2024 4:53:00 PM
6
min read
Is Software Supply Chain Security on Your Risk Register?


Is Software Supply Chain Security on Your Risk Register?
Aug 22, 2024 2:18:47 PM
4
min read
Six Things to Consider When Evaluating Software Security Solutions

Six Things to Consider When Evaluating Software Security Solutions
Jul 3, 2024 10:18:29 AM
2
min read
CISA's Secure Software Development Attestation Form: How SBOMs and Connected Device Security Can Help


CISA's Secure Software Development Attestation Form: How SBOMs and Connected Device Security Can Help
Jun 18, 2024 4:06:32 PM
4
min read
Strengthening IoT Security Through Secure by Design Principles


Strengthening IoT Security Through Secure by Design Principles
Jun 14, 2024 12:06:25 PM
4
min read
Three Steps Toward Better Software Supply Chain Security


Three Steps Toward Better Software Supply Chain Security
Apr 26, 2024 9:15:00 AM
4
min read
How to Choose the Right Java Library


How to Choose the Right Java Library
Mar 22, 2024 10:00:00 AM
4
min read
10 Java Libraries Every Developer Should Know About


10 Java Libraries Every Developer Should Know About
Mar 1, 2024 3:30:00 PM
3
min read
