Beyond Automation: Why Deep Binary Analysis is Critical for IoT Security Success


Beyond Automation: Why Deep Binary Analysis is Critical for IoT Security Success
May 7, 2025 2:23:12 PM
2
min read
The 2025 Verizon Data Breach Investigations Report: What It Means for Product and Supply Chain Security


The 2025 Verizon Data Breach Investigations Report: What It Means for Product and Supply Chain Security
May 6, 2025 4:50:32 PM
2
min read
Managing Open-Source Dependencies in IoT Software: Best Practices


Managing Open-Source Dependencies in IoT Software: Best Practices
Apr 9, 2025 6:43:15 AM
4
min read
Maximizing ROI with Dual-Layer Security Scanning: Source Code & Binary Analysis Best Practices


Maximizing ROI with Dual-Layer Security Scanning: Source Code & Binary Analysis Best Practices
Apr 9, 2025 6:16:57 AM
2
min read
Is SSDLC the Secret to Surviving Global Cybersecurity Regulations?


Is SSDLC the Secret to Surviving Global Cybersecurity Regulations?
Apr 4, 2025 2:16:26 PM
3
min read
Implementing End-to-End Software Supply Chain Security: Best Practices


Implementing End-to-End Software Supply Chain Security: Best Practices
Apr 3, 2025 12:39:09 PM
9
min read
Source Code vs. Binary Analysis: How Dual-Layer Security Protects Software Supply Chains


Source Code vs. Binary Analysis: How Dual-Layer Security Protects Software Supply Chains
Mar 14, 2025 5:41:32 PM
5
min read
How Artificial Intelligence is Revolutionizing Supply Chain Security in 2025


How Artificial Intelligence is Revolutionizing Supply Chain Security in 2025
Mar 7, 2025 1:27:57 PM
3
min read
The Business Case for IoT Security: Beecham Research Highlights the Growing Risks & Opportunities


The Business Case for IoT Security: Beecham Research Highlights the Growing Risks & Opportunities
Feb 28, 2025 1:57:12 PM
1
min read
Top 5 Software Supply Chain Security Threats in 2025
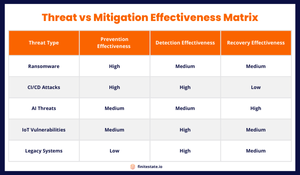

Top 5 Software Supply Chain Security Threats in 2025
Feb 25, 2025 12:36:56 PM
6
min read
How Effective Is Your Software Supply Chain Security? A Framework for Assessment


How Effective Is Your Software Supply Chain Security? A Framework for Assessment
Feb 13, 2025 2:27:32 PM
5
min read
CRA Compliance Made Simple: Addressing Common Software Supply Chain Security Obstacles


CRA Compliance Made Simple: Addressing Common Software Supply Chain Security Obstacles
Dec 6, 2024 3:52:36 PM
3
min read
Software Supply Chain Security Under the EU Cyber Resilience Act


Software Supply Chain Security Under the EU Cyber Resilience Act
Dec 6, 2024 1:36:44 PM
3
min read
Seven Practical Ways to Improve Your Software Supply Chain Maturity


Seven Practical Ways to Improve Your Software Supply Chain Maturity
Oct 4, 2024 3:13:14 PM
6
min read
All You Need to Know About Open Source License Compliance


All You Need to Know About Open Source License Compliance
Sep 4, 2024 4:53:00 PM
6
min read
