Navigating Open Source Compliance Rules & Component License Risks


Navigating Open Source Compliance Rules & Component License Risks
Sep 5, 2023 11:53:43 AM
3
min read
Where the SLSA 1.0 Release Shines (and Its Limitations)


Where the SLSA 1.0 Release Shines (and Its Limitations)
Apr 24, 2023 2:44:42 PM
4
min read
Why Is Gaining Visibility into Connected Devices So Challenging?

Why Is Gaining Visibility into Connected Devices So Challenging?
Dec 15, 2022 9:12:23 AM
2
min read
NIST Defines “Critical Software” — What it Means for Software Vendors and Device Manufacturers


NIST Defines “Critical Software” — What it Means for Software Vendors and Device Manufacturers
Jul 12, 2021 5:52:12 AM
3
min read
If you think your software is secure, get ready to prove it.


If you think your software is secure, get ready to prove it.
May 13, 2021 12:56:49 PM
6
min read
Security Processes for Connected Devices – Revisiting AppSec

Security Processes for Connected Devices – Revisiting AppSec
Mar 31, 2021 9:01:10 AM
3
min read
SolarWinds SUNBURST: An Intrusion, Attack, or Act of War?


SolarWinds SUNBURST: An Intrusion, Attack, or Act of War?
Dec 19, 2020 12:07:49 PM
5
min read
How We Can Prevent Supply Chain Attacks Like the One on SolarWinds


How We Can Prevent Supply Chain Attacks Like the One on SolarWinds
Dec 15, 2020 10:50:52 AM
4
min read
Detecting and Verifying New Vulnerabilities Across Your Product Portfolio
![]()
Detecting and Verifying New Vulnerabilities Across Your Product Portfolio
Dec 3, 2020 5:10:03 AM
3
min read
Key cybersecurity challenges for the energy sector—and how to address them


Key cybersecurity challenges for the energy sector—and how to address them
Nov 16, 2020 4:53:24 AM
5
min read
Revealing True Product Risk: Where Third Party Risk Assessments Are Falling Short

Revealing True Product Risk: Where Third Party Risk Assessments Are Falling Short
Sep 24, 2020 5:11:51 AM
3
min read
Vulnerability Trends in Connected Device Supply Chains
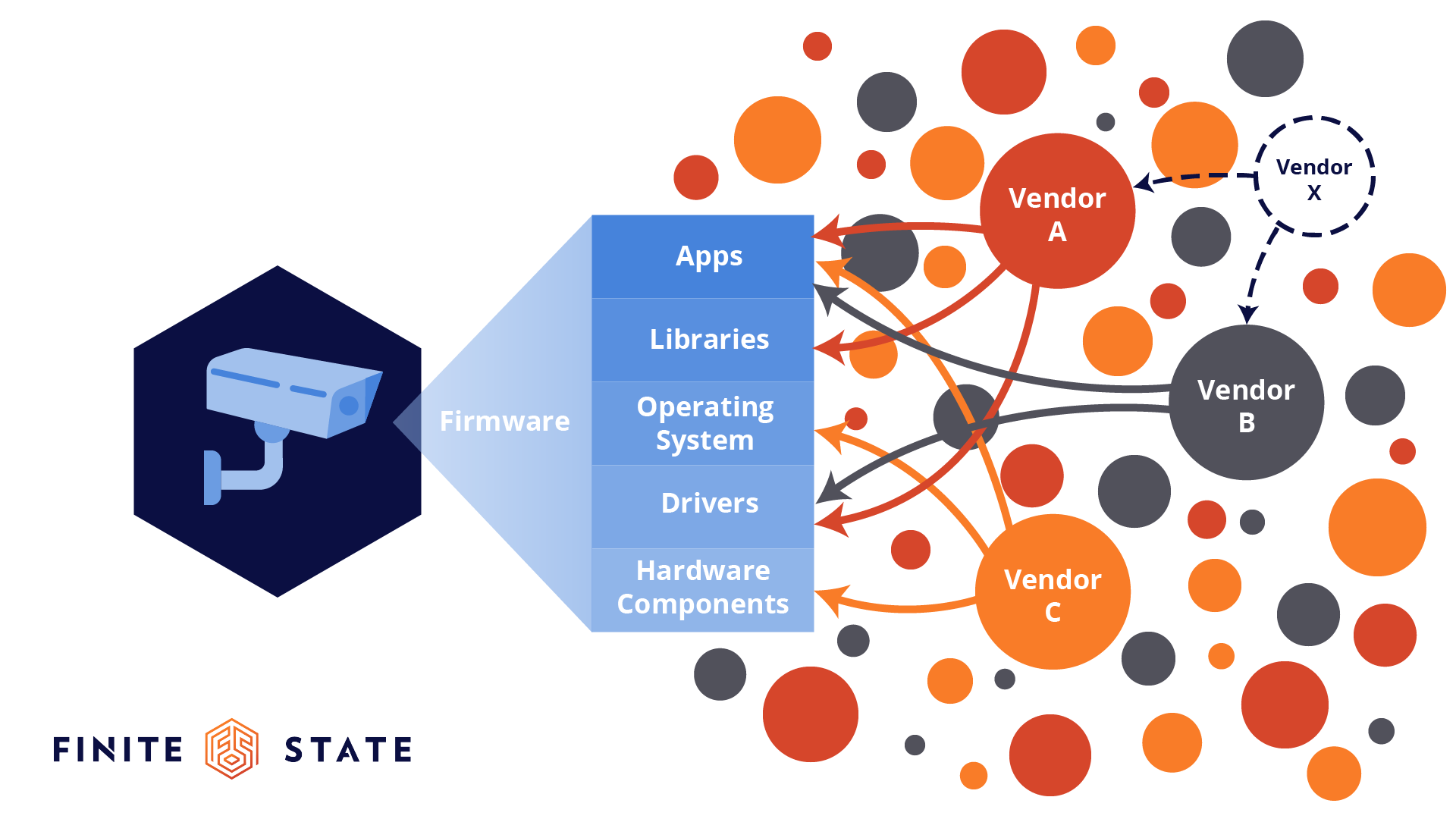

Vulnerability Trends in Connected Device Supply Chains
Aug 19, 2020 10:33:17 AM
1
min read
Securing IoT within the Financial Services and Insurance Industries
![]()
Securing IoT within the Financial Services and Insurance Industries
Sep 17, 2018 9:56:35 AM
3
min read
