Loading PDF preview…
Automotive Compliance & Security Management with Finite State
Finite State offers a comprehensive platform to help auto manufacturers and suppliers meet complex regulatory requirements, manage supply chain risk, and secure connected vehicles.
Categories
Related Resources

Finite State Cybersecurity Services
Finite State provides industry-leading cybersecurity services designed to help organizations navigate evolving regulations, enhance product security, ...
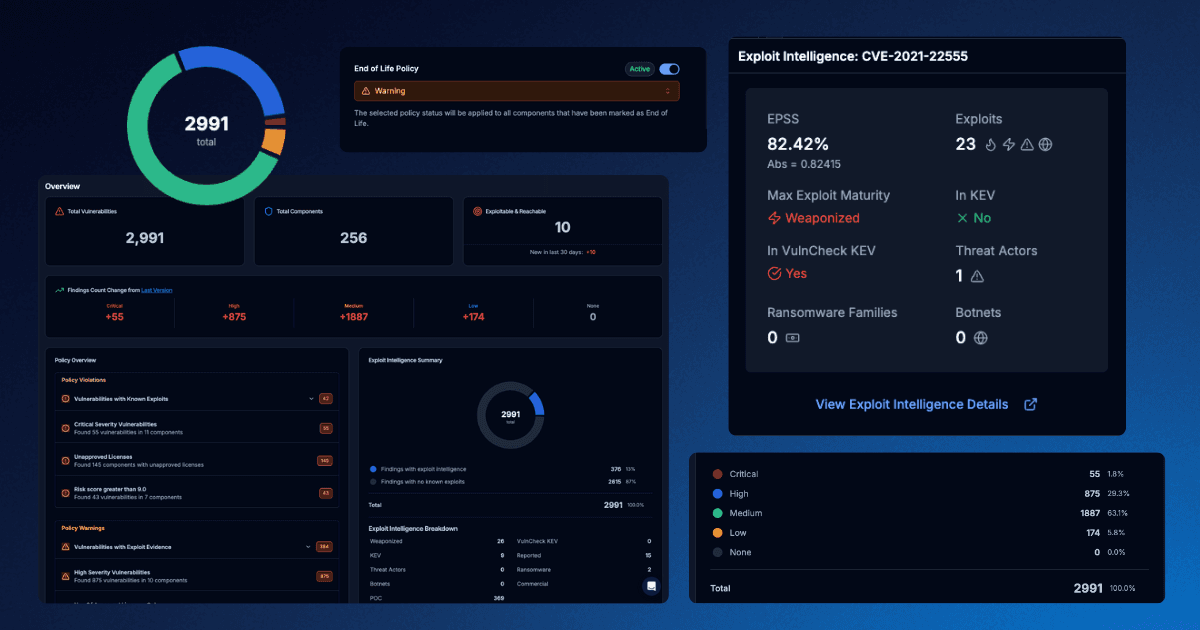
The Finite State Platform
Purpose-built for IoT and embedded systems, Finite State offers a centralized platform for securing the software supply chain of connected products th...
Finite State vs Black Duck
Compare Finite State vs. Black Duck: firmware/binary analysis, SBOM lifecycles, reachability-aware risks, and compliance built for connected products.
Ready to Level Up Your Security Knowledge?
Join thousands of security professionals learning from the best in the industry