Loading PDF preview…
Security Scanning & Analysis with Finite State
Finite State combines advanced binary software composition analysis (SCA), source code SCA, and binary static analysis security testing (SAST) for unique visibility into connected systems throughout the DevSecOps lifecycle.
Related Resources

Finite State Cybersecurity Services
Finite State provides industry-leading cybersecurity services designed to help organizations navigate evolving regulations, enhance product security, ...
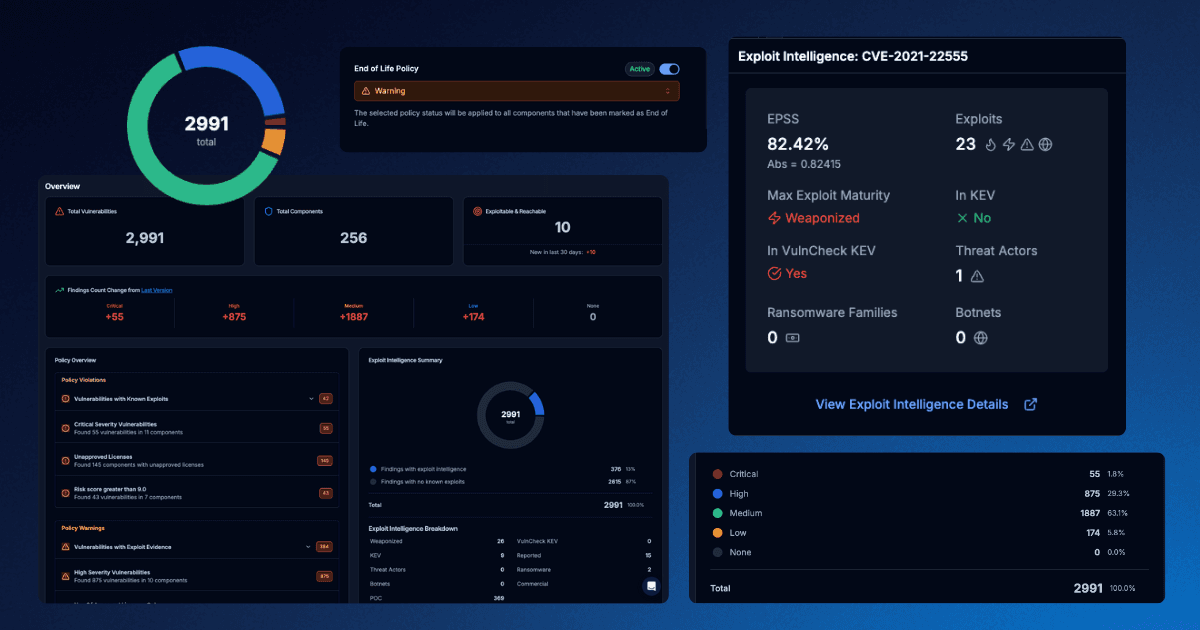
The Finite State Platform
Purpose-built for IoT and embedded systems, Finite State offers a centralized platform for securing the software supply chain of connected products th...
Finite State vs Black Duck
Compare Finite State vs. Black Duck: firmware/binary analysis, SBOM lifecycles, reachability-aware risks, and compliance built for connected products.
Ready to Level Up Your Security Knowledge?
Join thousands of security professionals learning from the best in the industry