Firmware | Software | Operational Technology
Find & Fix Vulnerabilities in Any Device
Built for the full product lifecycle. Engineered for the complexities of embedded systems.
%20(1).webp?width=719&height=683&name=platform%20images%20(500%20x%20475%20px)%20(1).webp)
Catch What Other Tools Can't
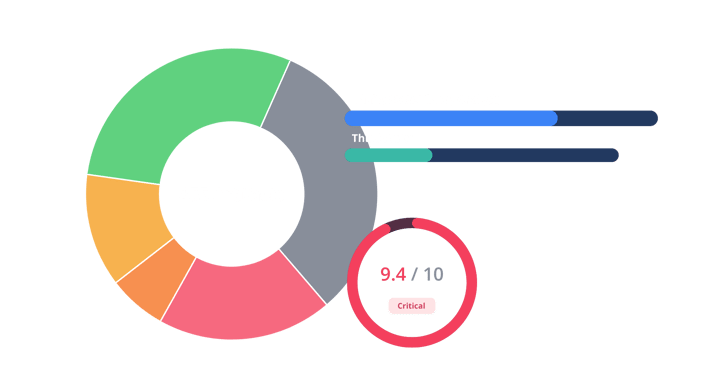
Dissect any source code or binary with market-leading precision to minimize false positives and get the most accurate vulnerability results so your team can prioritize and fix issues faster.
Finite State offers unmatched transparency into:
- Unique architectures
- Complex code
- Specific programming languages
Fix What Matters Most
Use context-aware guidance and risk-based details to efficiently prioritize action and seamlessly implement fixes using CI/CD integrations and auto PRs that your developers will love.
- Automatically correlate detected software components with CVEs from 200+ vulnerability and threat sources
- Continuously monitor and manage vulnerabilities throughout your product's lifespan
- Create and maintain highly-accurate SBOMs for any device
.webp?width=719&height=611&name=platform%20images%20small%20(1).webp)
.png?width=719&height=479&name=Untitled%20design%20(3).png)
Achieve Compliance-Readiness in Any Market
Leverage expertise from former U.S. government officials and get the support you need to tackle the evolving regulatory landscape with confidence.
- Create audit-ready reports to demonstrate product compliance
- Generate SBOMs with VDR/VEX vulnerability data in industry-standard formats (CycloneDX, SPDX)
- Employ continuous monitoring and alerting to meet regulatory reporting requirements
See Finite State in Action
Watch our recorded demo to discover how we're transforming product security across the entire software supply chain.
Platform Highlights
Powerful SBOM Generation
Comprehensive Threat Intelligence

Data-Driven Risk Scoring
Actionable Remediation Guidance

Extensive Software Composition Analysis

Customizable Reporting & Analytics
Easily generate reports to meet regulatory compliance requirements and share insights with internal and external stakeholders.
The binary SCA platform is not only user-friendly but also comprehensive, covering all the essential features one expects from an SBOM management tool. However, what truly distinguishes them is their personalized customer support.
The number of false positives and duplicates we see with free tools like Dependency Track vs what we see with Finite State showed us we need a paid tool.
Finite State provides a holistic approach to analyzing devices and the supply chain that underpins them... We are excited to form this partnership to further support our customers with shifting security left into the design and development of these innovative products.
Download our Product Security Solutions Buyer's Guide for expert insights to help you make an informed decision.

Latest From The Blog

Prioritize What’s Exploitable: Reachability Analysis For Connected Devices Has Arrived

The Hidden Costs of Post-Deployment Security Fixes and How to Avoid Them


