Maximizing ROI with Dual-Layer Security Scanning: Source Code & Binary Analysis Best Practices


Maximizing ROI with Dual-Layer Security Scanning: Source Code & Binary Analysis Best Practices
Apr 9, 2025 6:16:57 AM
2
min read
Is SSDLC the Secret to Surviving Global Cybersecurity Regulations?


Is SSDLC the Secret to Surviving Global Cybersecurity Regulations?
Apr 4, 2025 2:16:26 PM
3
min read
Implementing End-to-End Software Supply Chain Security: Best Practices


Implementing End-to-End Software Supply Chain Security: Best Practices
Apr 3, 2025 12:39:09 PM
9
min read
10 Ways to Streamline Developer Security Workflows


10 Ways to Streamline Developer Security Workflows
Mar 21, 2025 6:11:41 PM
7
min read
A Technical Guide to Cross-Framework Compliance for IoT Manufacturers

A Technical Guide to Cross-Framework Compliance for IoT Manufacturers
Mar 17, 2025 7:36:01 PM
7
min read
Source Code vs. Binary Analysis: How Dual-Layer Security Protects Software Supply Chains


Source Code vs. Binary Analysis: How Dual-Layer Security Protects Software Supply Chains
Mar 14, 2025 5:41:32 PM
5
min read
How Artificial Intelligence is Revolutionizing Supply Chain Security in 2025


How Artificial Intelligence is Revolutionizing Supply Chain Security in 2025
Mar 7, 2025 1:27:57 PM
3
min read
The Business Case for IoT Security: Beecham Research Highlights the Growing Risks & Opportunities


The Business Case for IoT Security: Beecham Research Highlights the Growing Risks & Opportunities
Feb 28, 2025 1:57:12 PM
1
min read
Top 5 Software Supply Chain Security Threats in 2025
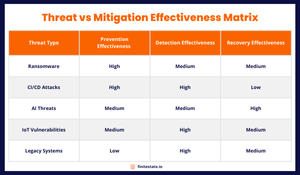

Top 5 Software Supply Chain Security Threats in 2025
Feb 25, 2025 12:36:56 PM
6
min read
The EU Radio Equipment Directive (RED): A Deep Dive into Article 3.3 and Its Implications for IoT Manufacturers


The EU Radio Equipment Directive (RED): A Deep Dive into Article 3.3 and Its Implications for IoT Manufacturers
Feb 14, 2025 4:34:45 PM
4
min read
How Effective Is Your Software Supply Chain Security? A Framework for Assessment


How Effective Is Your Software Supply Chain Security? A Framework for Assessment
Feb 13, 2025 2:27:32 PM
5
min read
Understanding Secure by Design: An EU CRA Guide for IoT Manufacturers
.png?width=761&height=403&name=Security%20by%20Design%20(EU%20CRA).png)
.png?width=761&height=403&name=Security%20by%20Design%20(EU%20CRA).png)
Understanding Secure by Design: An EU CRA Guide for IoT Manufacturers
Jan 28, 2025 6:30:10 PM
5
min read
Executive Order 14144 Strengthens US Cybersecurity: What IoT Manufacturers Need to Know


Executive Order 14144 Strengthens US Cybersecurity: What IoT Manufacturers Need to Know
Jan 24, 2025 12:31:47 PM
3
min read
Cybersecurity Risk Assessments & The EU CRA


Cybersecurity Risk Assessments & The EU CRA
Jan 24, 2025 8:00:00 AM
2
min read
The Hidden Costs of Free Vulnerability Scanners


The Hidden Costs of Free Vulnerability Scanners
Jan 23, 2025 7:06:37 PM
4
min read

.png?width=812&height=509&name=fs-background-texture-02-1%20(blog).png)